Cryptographic hashing functions form the mathematical foundation of blockchain technology, ensuring data integrity, immutability, and security across distributed networks. Understanding these algorithms is essential for grasping how blockchains maintain trust without central authorities and why tampering with blockchain data is computationally infeasible. This exploration examines the critical role of hashing in blockchain architecture and its practical implications.
A hash function is a mathematical algorithm that takes input data of any size and produces a fixed-size output called a hash or digest. Cryptographic hash functions possess specific properties that make them suitable for blockchain applications: they are deterministic (same input always produces same output), quick to compute, collision-resistant (practically impossible to find two inputs producing the same output), and exhibit the avalanche effect where tiny input changes produce dramatically different outputs.
SHA-256, part of the Secure Hash Algorithm family developed by the NSA, serves as Bitcoin's primary hashing algorithm. It produces 256-bit (64-character hexadecimal) outputs regardless of input size. Bitcoin uses SHA-256 in multiple contexts: hashing transaction data, linking blocks through chain references, and as the basis for proof-of-work mining. The algorithm's security has withstood extensive cryptanalytic scrutiny, though quantum computing poses theoretical future concerns.
The relationship between blocks in a blockchain illustrates hashing's fundamental importance. Each block contains the hash of the previous block's header, creating an immutable chain stretching back to the genesis block. This structure means altering any historical transaction would change that block's hash, breaking the chain and making tampering immediately detectable. The computational cost of recalculating all subsequent hashes makes rewriting blockchain history economically prohibitive.
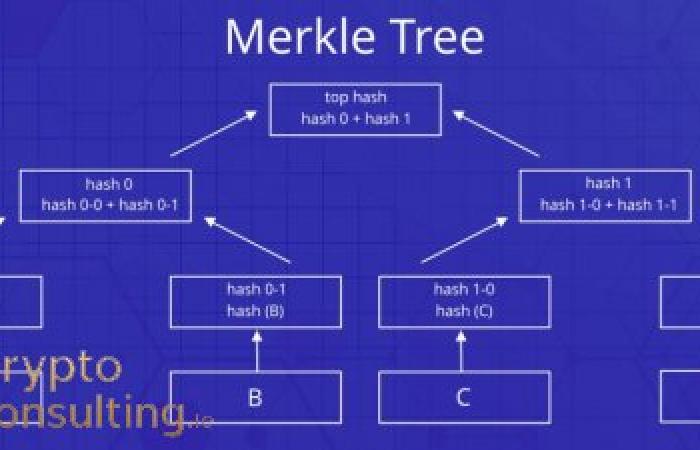
Merkle trees, named after computer scientist Ralph Merkle, represent another critical hashing structure in blockchain technology. These binary tree structures efficiently summarize all transactions in a block through hierarchical hashing. Transaction hashes are paired and hashed together repeatedly until a single Merkle root remains, which is included in the block header. This structure enables efficient verification that specific transactions are included in blocks without downloading entire blockchain datasets.
Light clients and Simplified Payment Verification (SPV) nodes leverage Merkle trees to verify transactions without storing complete blockchain data. By obtaining block headers and Merkle proofs, light clients can cryptographically verify transaction inclusion with minimal data requirements. This capability is crucial for mobile wallets and other resource-constrained applications requiring transaction verification without full node operation.
Beyond Bitcoin's SHA-256, different blockchains employ various hashing algorithms. Ethereum uses Keccak-256, selected through the SHA-3 competition. Litecoin uses Scrypt, designed to be memory-hard and resistant to specialized mining hardware. These algorithm choices reflect different security priorities, hardware considerations, and approaches to mining centralization concerns.
Hashing also enables efficient data structures like hash tables and Merkle Patricia tries, which Ethereum uses to store state information. These structures allow quick lookups and verifications while maintaining cryptographic security guarantees. The combination of these techniques enables blockchains to efficiently manage massive datasets while preserving security properties.
Security considerations around hashing remain paramount. While SHA-256 and other modern hash functions are considered secure against classical computing attacks, quantum computers may eventually threaten their collision resistance through Grover's algorithm. Blockchain developers are monitoring quantum computing progress and researching post-quantum cryptographic alternatives to ensure long-term security.
The practical implications of cryptographic hashing extend throughout blockchain applications. Smart contract addresses derive from hashing public keys. Digital signatures rely on hashing message contents. Proof-of-work systems use repeated hashing for consensus. Understanding hashing is therefore fundamental to comprehending blockchain security models and why these systems can maintain trust in adversarial environments without central authorities.

